Assumptions
It is assumed that the Trusted Root (CA) certificate is installed on the target server(s). If the CA certificate is not installed on the server/client at the time you try to install the web server certificate, the installation will fail.
Pre-requisites
The high-level overview of the tasks that are involved in installing web server certificates on web application servers and clients that are located outside Active Directory domains are:
· Ensure the Trusted Root (CA) certificate is installed.
Ø If the web server where the certificate is being installed is not part of Windows Active Directory then we need to ensure that the certificate for the trusted root certificate authority is installed on the target server. This is required to validate the server certificate. The Certificate Chain will be provided by “GITRM-Information Security Operations” team OR could be downloaded from the Web Enrollment Site itself.
· Depending on applications, the “Chain of Trust” might have to be installed in application-specific trusted store. Please consult your application vendor to how to accomplish this.
· Use appropriate inf file to create a certificate request from the Enterprise CA;
WebServerStandarddSAN.inf – for standard Web Server certificate requiring SAN
WebServerMutualAuthenticationSAN.inf – for Mutual Authentication Web Server certificate requiring SAN
· While submitting the CSR from web enrollment site, ensure accurate certificate templates are chosen depending on types of certificates being requested
Web Server Standard (PKI QA ADCS 2012) – for standard Web Server certificate requiring SAN
Web Server Mutual Authentication (PKI QA ADCS 2012) – for Mutual Authentication Web Server certificate requiring SAN
Requesting a web server certificate with SANs using certutil
It is best practice to request the certificate from the server that it will be installed on.
1) Depending on the type of certificate, you are requesting will determine which of the following inf files you will need to use: Standard Server Authentication certificate or Mutual Authentication certificate.
For a certificate that will be used in a one way trust and provide Server Authentication use the WebServerStandardSAN.inf – for standard Web Server certificate requiring subject alternate name(s)
=========================================================================
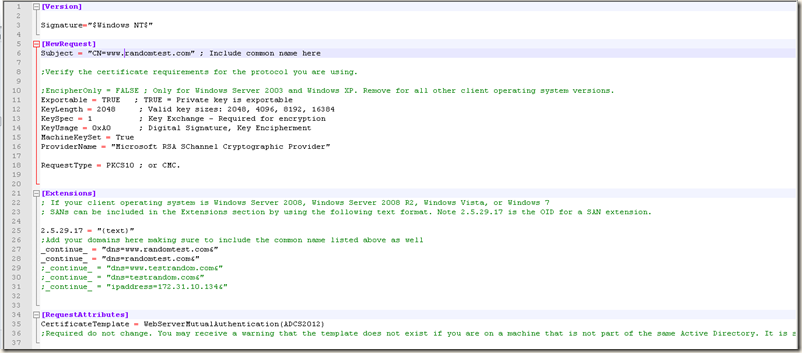
WebServerStandardSAN.inf
[Version]
Signature="$Windows NT$"
[NewRequest]
Subject = "CN=www.randomtest.com" ; Include common name here
;Verify the certificate requirements for the protocol you are using.
;EncipherOnly = FALSE ; Only for Windows Server 2003 and Windows XP. Remove for all other client operating system versions.
Exportable = TRUE ; TRUE = Private key is exportable
KeyLength = 2048 ; Valid key sizes: 1024, 2048, 4096, 8192, 16384
KeySpec = 1 ; Key Exchange – Required for encryption
KeyUsage = 0xA0 ; Digital Signature, Key Encipherment
MachineKeySet = True
ProviderName = "Microsoft RSA SChannel Cryptographic Provider"
RequestType = PKCS10 ; or CMC.
[Extensions]
; If your client operating system is Windows Server 2008, Windows Server 2008 R2, Windows Vista, or Windows 7
; SANs can be included in the Extensions section by using the following text format. Note 2.5.29.17 is the OID for a SAN extension.
2.5.29.17 = "{text}"
;Add your domains here making sure to include the common name listed above as well
_continue_ = "dns=www.randomtest.com&"
_continue_ = "dns=randomtest.com&"
;_continue_ = "dns=www.testrandom.com&"
;_continue_ = "dns=testrandom.com&"
;_continue_ = "ipaddress=172.31.10.134&"
[RequestAttributes]
CertificateTemplate = WebServerStandard(ADCS2012)
;Required do not change. You may receive a warning that the template does not exist if you are on a machine that is not part of the same Active Directory. It is safe to ignore that message.
====================================================================
For a certificate that will be used in a two way trust and provide Client and Server Authentication use the WebServerMutualAuthenticationSAN.inf – for Mutual Authentication Web Server certificate requiring subject alternate name(s)
==========================================================================
WebServerMutualAuthenticationSAN.inf
[Version]
Signature="$Windows NT$"
[NewRequest]
Subject = "CN=www.randomtest.com" ; Include common name here
;Verify the certificate requirements for the protocol you are using.
;EncipherOnly = FALSE ; Only for Windows Server 2003 and Windows XP. Remove for all other client operating system versions.
Exportable = TRUE ; TRUE = Private key is exportable
KeyLength = 2048 ; Valid key sizes: 2048, 4096, 8192, 16384
KeySpec = 1 ; Key Exchange – Required for encryption
KeyUsage = 0xA0 ; Digital Signature, Key Encipherment
MachineKeySet = True
ProviderName = "Microsoft RSA SChannel Cryptographic Provider"
RequestType = PKCS10 ; or CMC.
[Extensions]
; If your client operating system is Windows Server 2008, Windows Server 2008 R2, Windows Vista, or Windows 7
; SANs can be included in the Extensions section by using the following text format. Note 2.5.29.17 is the OID for a SAN extension.
2.5.29.17 = "{text}"
;Add your domains here making sure to include the common name listed above as well
_continue_ = "dns=www.randomtest.com&"
_continue_ = "dns=randomtest.com&"
;_continue_ = "dns=www.testrandom.com&"
;_continue_ = "dns=testrandom.com&"
;_continue_ = "ipaddress=172.31.10.134&"
[RequestAttributes]
CertificateTemplate = WebServerMutualAuthentication(ADCS2012)
;Required do not change. You may receive a warning that the template does not exist if you are on a machine that is not part of the same Active Directory. It is safe to ignore that message.
2) The inf file should be provided to the user generating the request. Make following changes to the inf file;
3) Under [NewRequest] section in the *.inf file, for subject, put in the FQDN of the server or URI
Subject = “FQDN of the web service application”
4) Under [Extensions] section in the *.inf file, make changes to reflect the SANs being requested;
[Extensions]
2.5.29.17 = "{text}"
_continue_ = "dns=www.randomtest.com&"
_continue_ = "dns= randomtest.com&"
_continue_ = "dns=www1.randomtest.com&"
5) Bring up command prompt in Administrator user context and navigate to the folder where you would like to create the certificate request.
For standard Web server certificate request;
C:\SAN Testing> certreq -new WebServerStandardSAN.inf nameoftheserver.req
For Mutual Authentication Server certificate request;
C:\SAN Testing> certreq -new WebServerMutualAuthenticationSAN.inf nameoftheserver.req
6) Once the above command is issued, the certificate request is generated in the directory. CSR must be submitted through web enrollment site to be signed by Subordinate Issuing CA.

Certificate Request
The Certificate Signing Request (CSR) on the target server has to be created on the target server prior to following below steps.
7) Navigate to the MS-PKI web enrollment site from the web browser on the target server:
8) When prompted, Put in your credential to login to MS-PKI web enrollment site and click OK
9) Click on Request a certificate.
10) Click Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file..
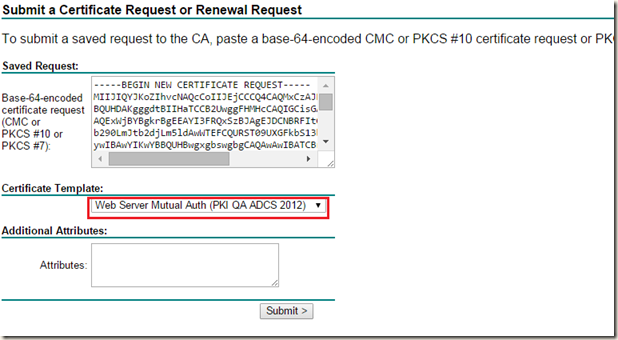
11) Under Saved Request paste in your CSR that was generated previously.
12) Ensure that under Certificate Template drop-down menu proper certificate template is selected;
For Web Server Standard with SANs, select Web Server Std (ADCS 2012)
For Web Server Mutual Authentication with SANs, select Web Server Mutual Auth (ADCS 2012)
Click Submit.
13) Contact the Certificate and Certificate and Key Management team with the Request ID (supplied in the Certificate Pending response window) for certificate issuance.
Notify Management.CertificateKey@random.com team about the submission of CSR (with Request ID)
Certificate Retrieval and Installation
Once the request has been approved and CSR signed, you can now retrieve and install the new certificate.
1) Return to the MS PKI web enrollment site and select View the status of the pending certificate request.
2) Click on the certificate request that you requested for the Web Service application server,
NOTE: If the certificate request has not yet been approved or denied, you will receive this message window.
3) Select the Yes button in response to the access confirmation pop-up window.
4) Select Base 64 encoded and click Download Certificate.
Note: application owner should know the type of certificate they need to download (DER encoded or Base 64 encoded).
5) Save the certificate in desired location. The signed certificate request needs to be provided to the web server administrator who will then install the certificate in the Web server.
6) Go back to the page; Select Base 64 encoded and click Download Certificate Chain
7) Save the certificate in desired location. The chain needs to be installed and trusted in the WEB server for the issued Web server certificate to work properly.
14) Copy *.cer to the same directory (in the Web Server) where the *.req file is located and issue the following command. Perform Web Server application-specific procedure to complete the certificate request.
C:\SAN Testing> certreq –accept nameoftheserver.cer
Export the Certificate with the Private Key
If you need to export the certificate with the private key, effectively creating a PCKS#12 file having a .pfx file extension, follow steps below;
1) The certificate can now be exported from the computer personal certificate store it was installed in.
a) Launch an MMC console and add the Certificates snap-in
b) When prompted, ensure you select that you want to manage certificates for “Computer Account > Local computer”.
c) Right-click on the certificate, and select export from the All Tasks context menu.
2) Ensure you export the private key with the certificate by selecting the `Yes, export the private key radio button. Specify a password to protect the private key, and save the certificate to the designated certificates folder.
3) Check the radio button labeled Personal Information Exchange – PKCS #12 (.PFX). Ensure you do not check the box to Include all certificates in the certification path if possible.
4) Since you have requested that the private key be exported, you must secure it with a password.
Enter a password (don’t forget it), and then click Export.
5) You will now be prompted for a path and name to export the certificate to.
Click Save
6) Click Finish and you’re done.